Today's subject: VTP, and why you shouldn't use it in your switched network. Let's dive in.
What is VTP?
VTP stands for VLAN trunking protocol. It's a Cisco proprietary protocol that allows for the automatic propagation of layer 2 VLANs across a switched network. VTP is commonly used in the Cisco Catalyst switch platform, but it's not a recommended feature to use in your production network.
Functions of VTP
This section will discuss how VTP operates in a network.
VLAN propagation
The idea of VTP is to automatically propagate VLANs from one switch to another switch across an 802.1Q trunk.
VTP advertisements
Switches propagate VLANs to each other via an 802.1Q trunk. VTP advertisements are sent as multicast ethernet frames on destination MAC address 0100.0ccc.cccc across the trunk.
When switches receive VTP frames, they synchronize their configuration revision number to their neighbor on the trunk link.
Configuration revision numbers
Switches keep track of their VLAN configuration with the use of a configuration revision number. If you run a show vtp status on your Cisco Catalyst switch, you will find the configuration revision number.
D1#show vtp status
** Configuration Revision : 13 **
If a switch receives a VTP advertisement where it sees a higher configuration revision number than it already has, then it will synchronize itself to that higher configuration revision number.
Any time you create, modify, or delete VLANs on a VTP server, that configuration revision number is incremented by 1.
VTP versions
There are three versions of VTP.
VTP version one and two support normal range VLANs (1-1005). The modes are server/client/transparent.
VTP version three supports password encryption, the entire range of VLANs (1-4094), and also supports multiple spanning tree (MST). The modes are primary server/client/transparent/off.
Below is a show vtp status command output example. You can see the VTP version and supported VTP versions on the switch where this command was executed.
D1#show vtp status
** VTP Version capable : 1 to 2 **
** VTP version running : 2 **
VTP domain
Switches can only be part of one VTP domain. A VTP domain defines the switches in the group together where VLANs should be synchronized. The VTP domain is defined on each switch in global configuration mode.
Below is a show vtp status output where you can see an example of a configured VTP domain name.
D1#show vtp status
VTP Version capable : 1 to 2
VTP version running : 2
** VTP Domain Name : kmohr **
VTP modes
Versions 1 and 2 have the following operating modes:
Server - Can create, modify, or delete VLANs. Forwards VTP advertisements.
Client - Synchronizes itself to VTP servers. Cannot create, modify, or delete VLANs. Receives VTP advertisements but does not actively forward them.
Transparent - Does not synchronize itself. Forwards VTP advertisements downstream to other devices in the VTP domain.
Below is a show vtp status command output where you can see the operating mode of an example switch utilizing VTP.
D1#show vtp status
VTP Version capable : 1 to 2
VTP version running : 2
VTP Domain Name : kmohr
VTP Pruning Mode : Disabled
VTP Traps Generation : Disabled
Device ID : 0001.42C2.9D00
Configuration last modified by 0.0.0.0 at 3-1-93 00:07:14
Local updater ID is 0.0.0.0 (no valid interface found)
Feature VLAN :
--------------
** VTP Operating Mode : Server **
Benefits of VTP
There are some benefits to using VTP in a network. Below are the reasons why a network engineer would consider using VTP.
Automation
In a layer 2 switched network where there's no VTP, network engineers have to spend time going across each switch and manually configuring VLANs on those switches. With the use of VTP, you go to one switch only, which acts as a "server", where you create the VLANs, and those VLANs get propagated to "clients" automatically.
Scalability
Since VTP reduces the administrative overhead of creating VLANs, VTP makes VLAN creation more scalable. You can define a large amount of VLANs and scale out these VLANs across the network quickly. Using VTP can reduce the overhead required to manage VLANs on a large network as you only have to go to one device and define the VLANs there.
Drawbacks of VTP
VTP has a lot more drawbacks than benefits. I'll discuss those drawbacks below.
Version issues
There are three versions of VTP. Version 1 and 2 have three operating modes: server, client, and transparent. Version 3 has five operating modes: primary server, secondary server, client, transparent, and off.
Version 1 and 2 only support the normal range of VLANs (1-1005), while version 3 supports the entire range (1-4094) of VLANs. Unfortunately, VTP version 3 is only supported on very recent models of Cisco Catalyst switches. If you are running Catalyst hardware running Cisco IOS versions older than 12.2 SE, then your switch won't support VTP version 3. Now granted, if you're running a switch with an older IOS version than 12.3 SE, then you should consider upgrading your network infrastructure, as you're most likely running EOL hardware, and that's a big problem.
Nevertheless, not all Cisco Catalyst switches support running Version 3, which is a problem if you need to create any VLANs in the extended VLANs range (1006-4094).
Version 1 and 2 Propagation Problems
VTP versions 1 and 2 can be problematic. When you take into account the fact that switches synchronize VLAN configurations based on configuration revision numbers, if one switch has a higher configuration revision number than another, then that switch will synchronize itself with the other switch.
So, if you have a switch that you put in place where you recently created and deleted a lot of VLANs - if you did not put it in client mode before joining it to the VTP domain, then you run the risk of causing all those VLANs you created to synchronize across your VTP domain, which may lead to disastrous results.
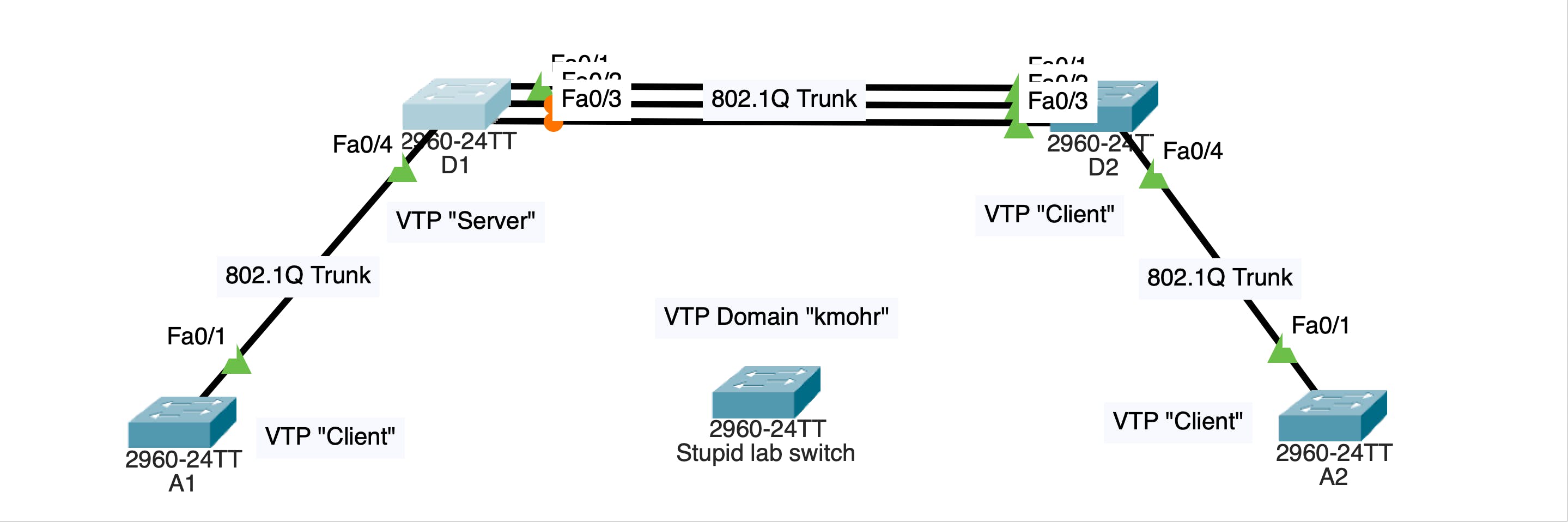
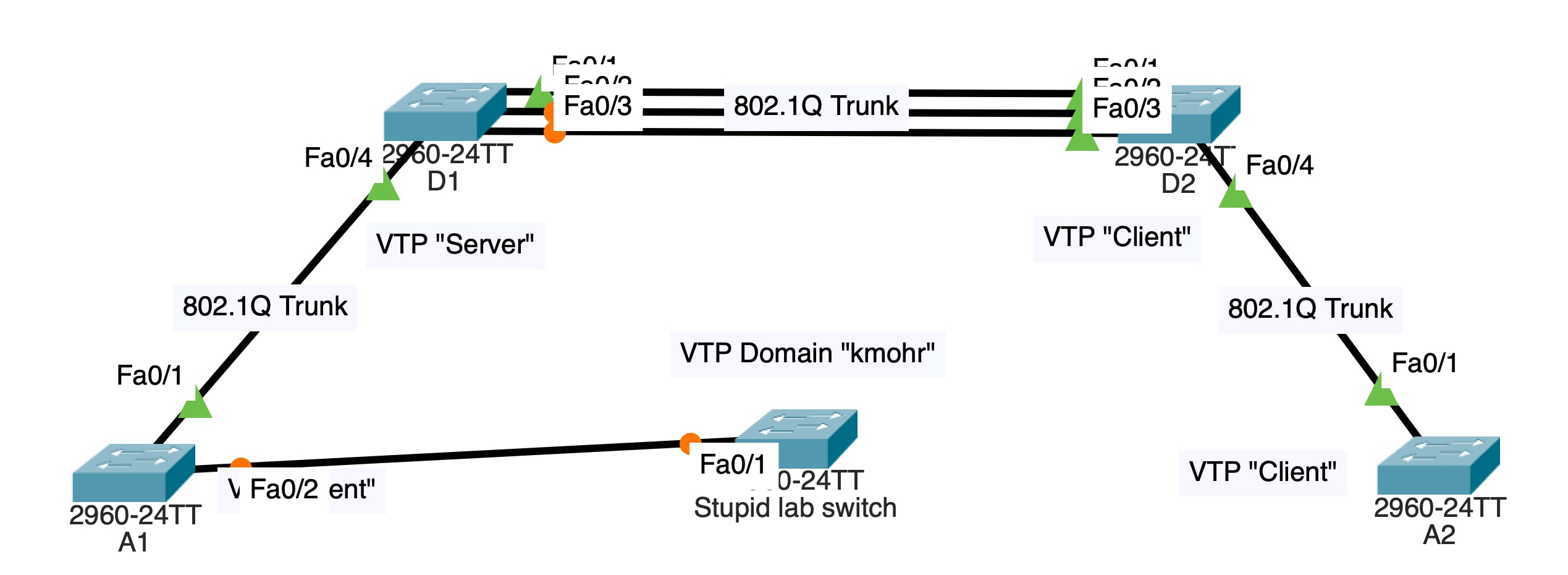
Here's a perfectly normal VTP domain.
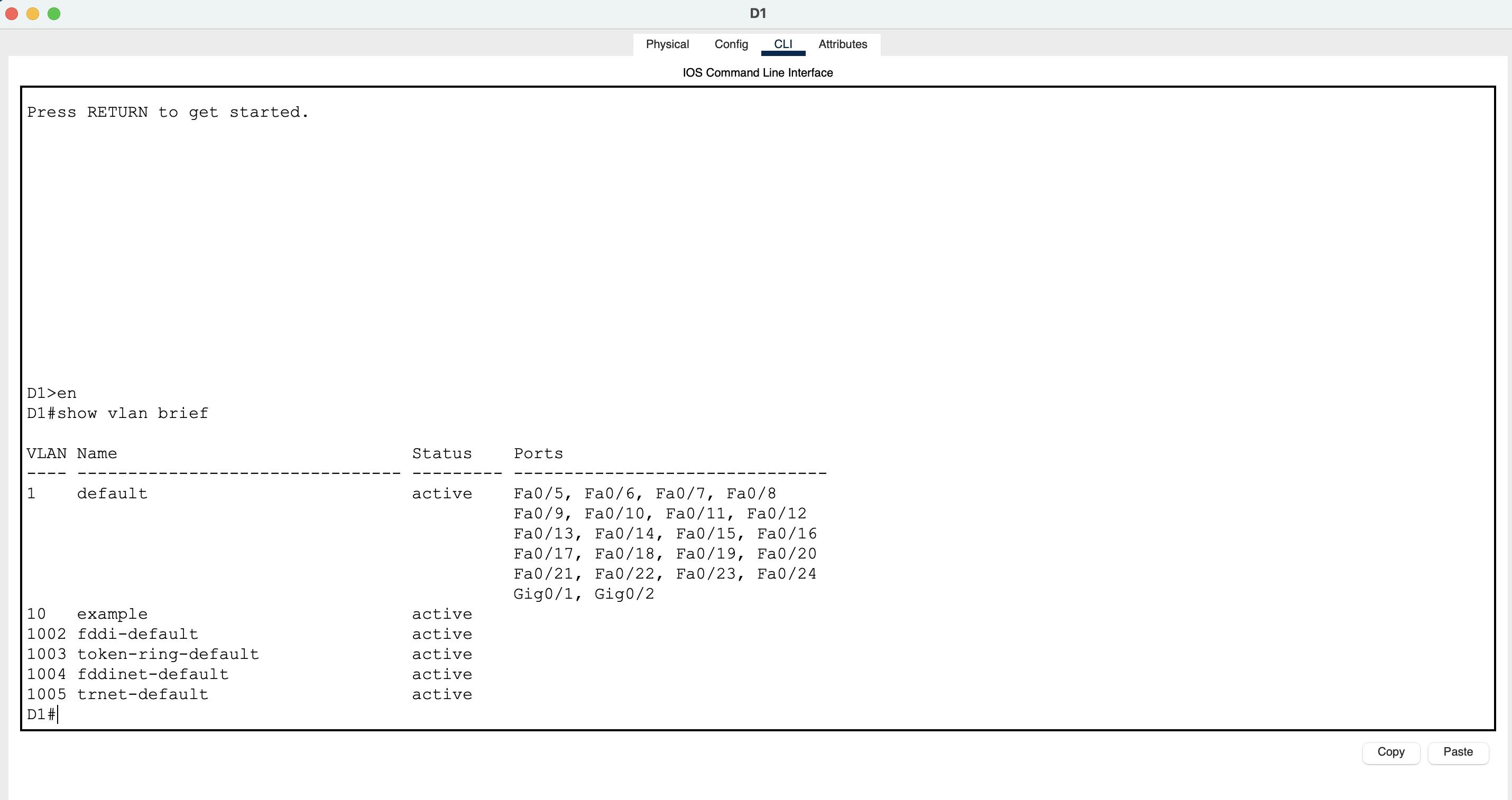
Here's a show vlan brief and show vtp status from the D1 switch. Notice that the D1 switch' operating mode is server.
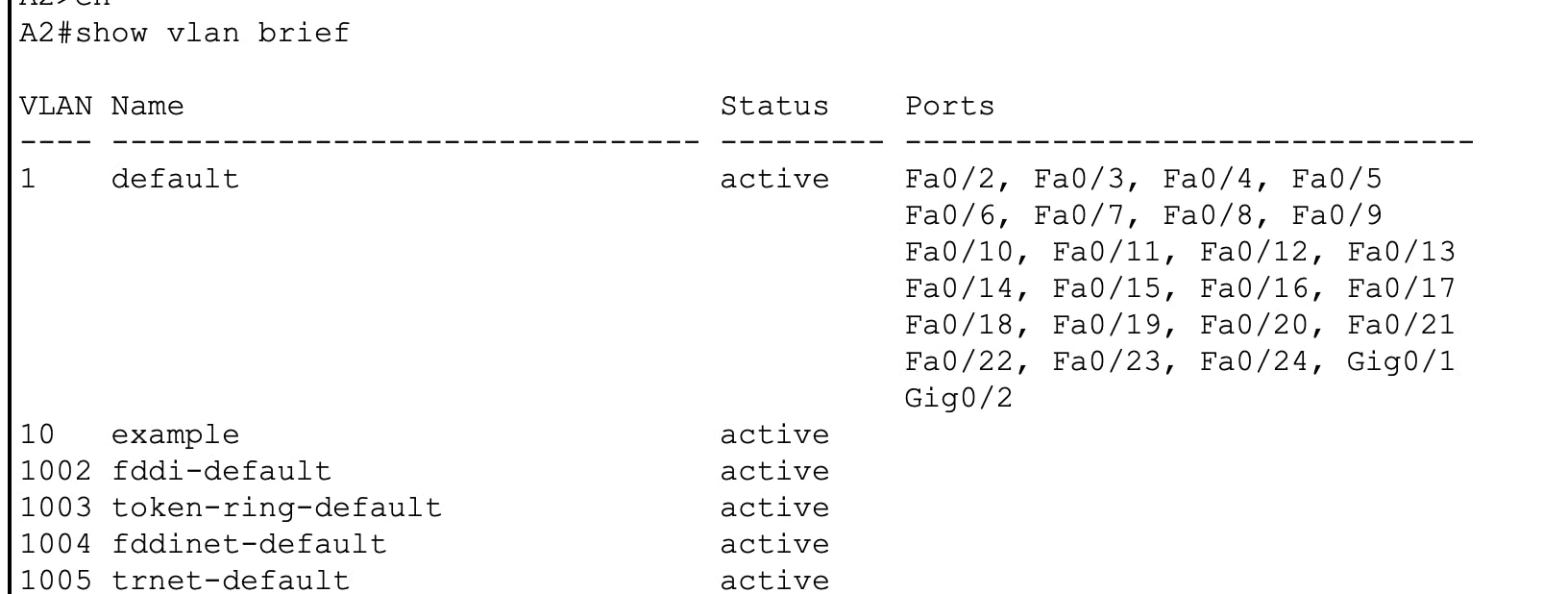
Here's an output of show vlan brief and show vtp status on A2 - notice its VTP operating mode is client.
Notice in the topology I have a switch called "Stupid lab switch". Now imagine that I configured that switch on a bench for lab testing, and I forgot to erase my VLAN.dat file. I also neglected to set the switch' role to VTP client.
Watch what happens when I plug "Stupid lab switch" into switch A1, which operates as a VTP client.
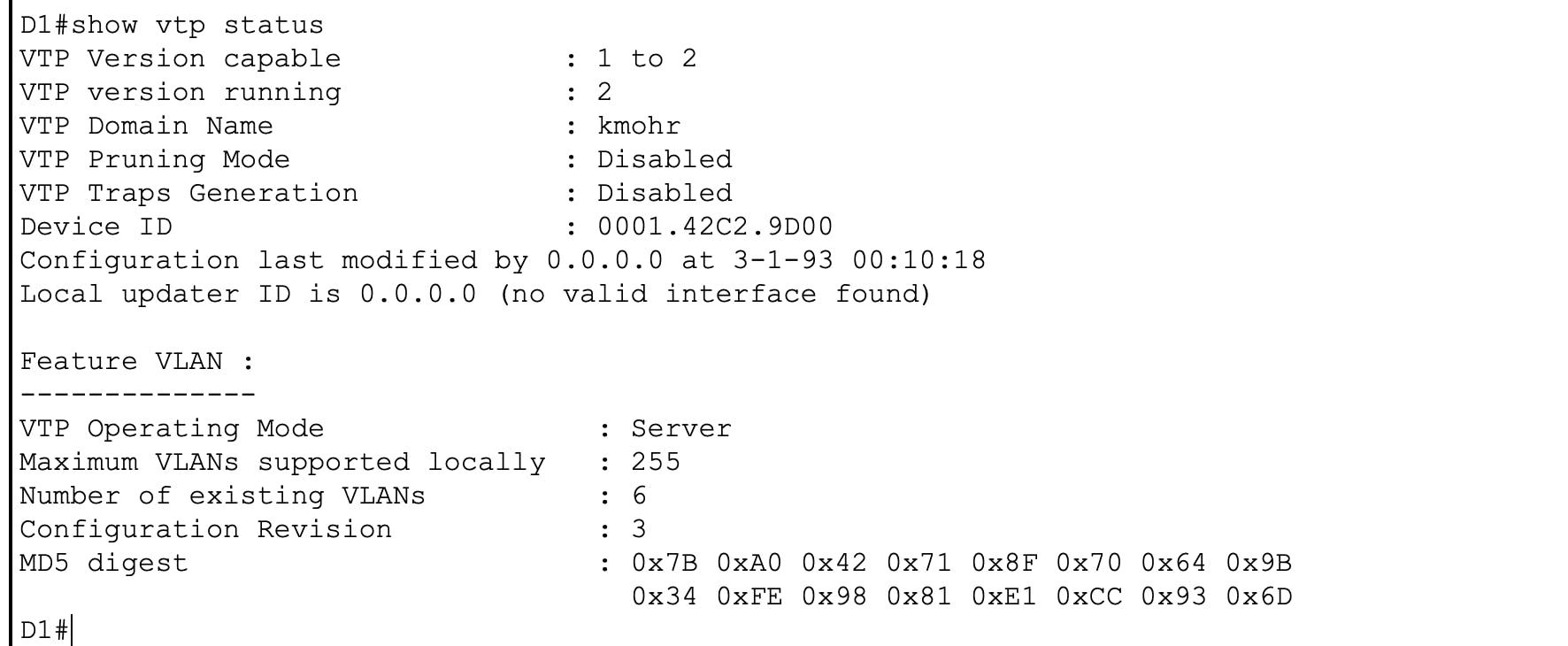
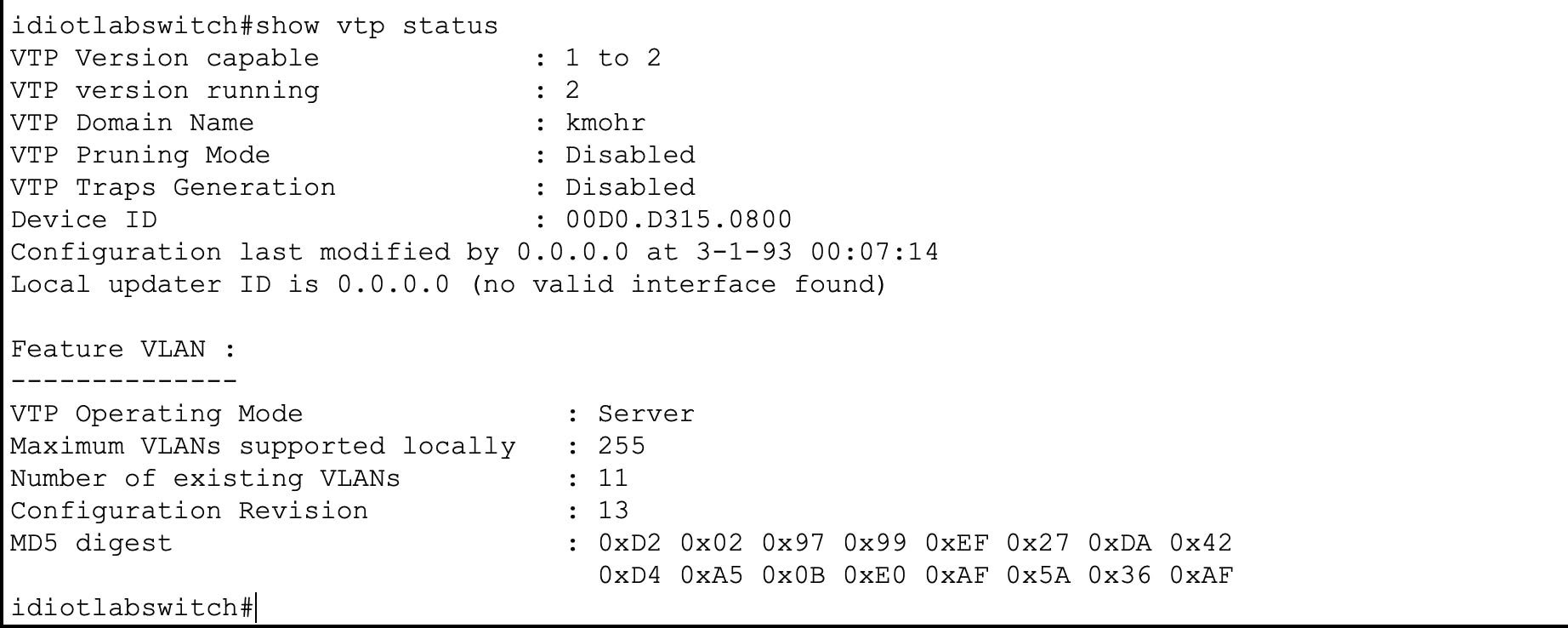
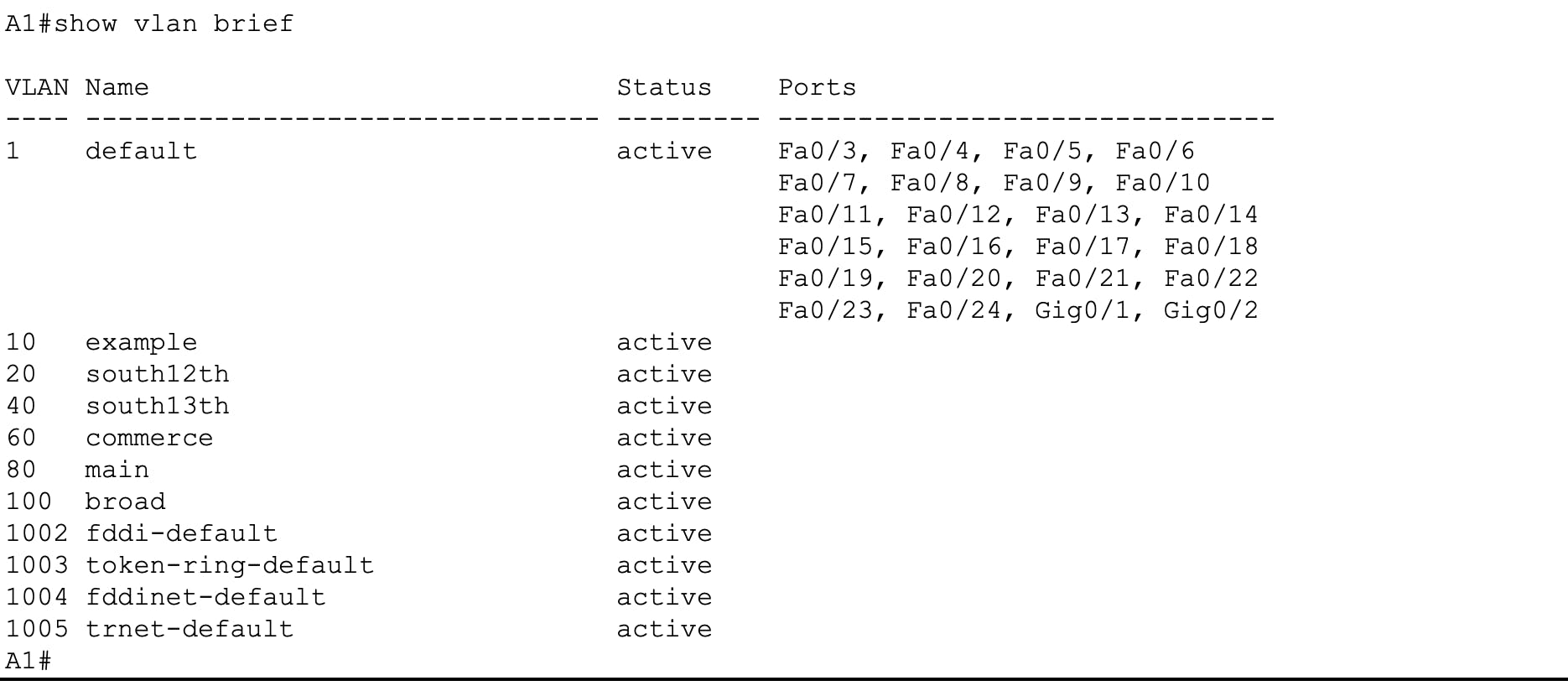
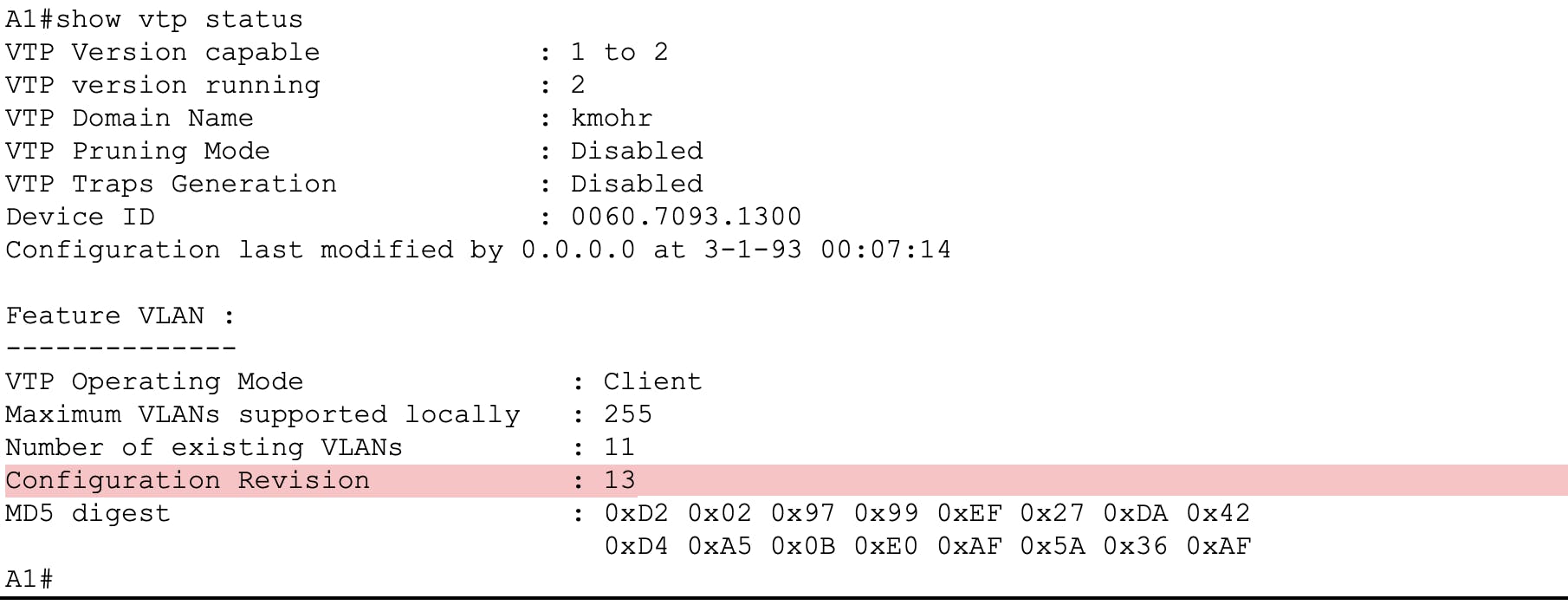
Below is a show vtp status output of the "Stupid lab switch". Notice how its configuration revision number is 13.
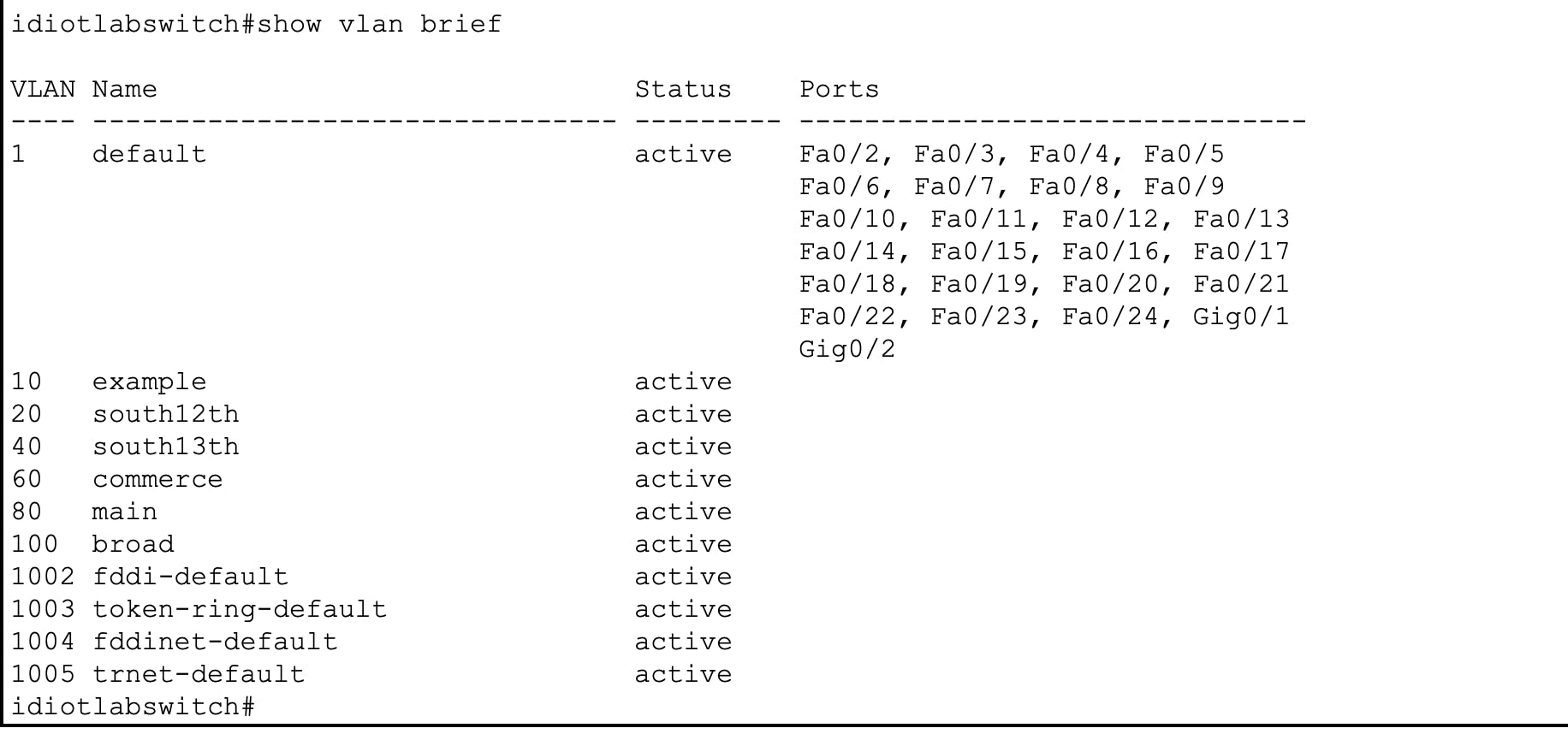
Below is a show vlan brief output from the same switch. There's a lot of VLANs in the output.
Below is a show vlan brief and show vtp status output from switch A1. Check out what happened - some VLANs got created on that switch and its configuration revision number is now 13.
Do you see what happened here? When I added my lab switch to the topology, my A1 switch synced with the lab switch. But wait! There's more! The ENTIRE topology is now synced with the lab switch...even the VTP SERVER!!! Check out the screenshots from D1's show vtp status and show vlan brief outputs.
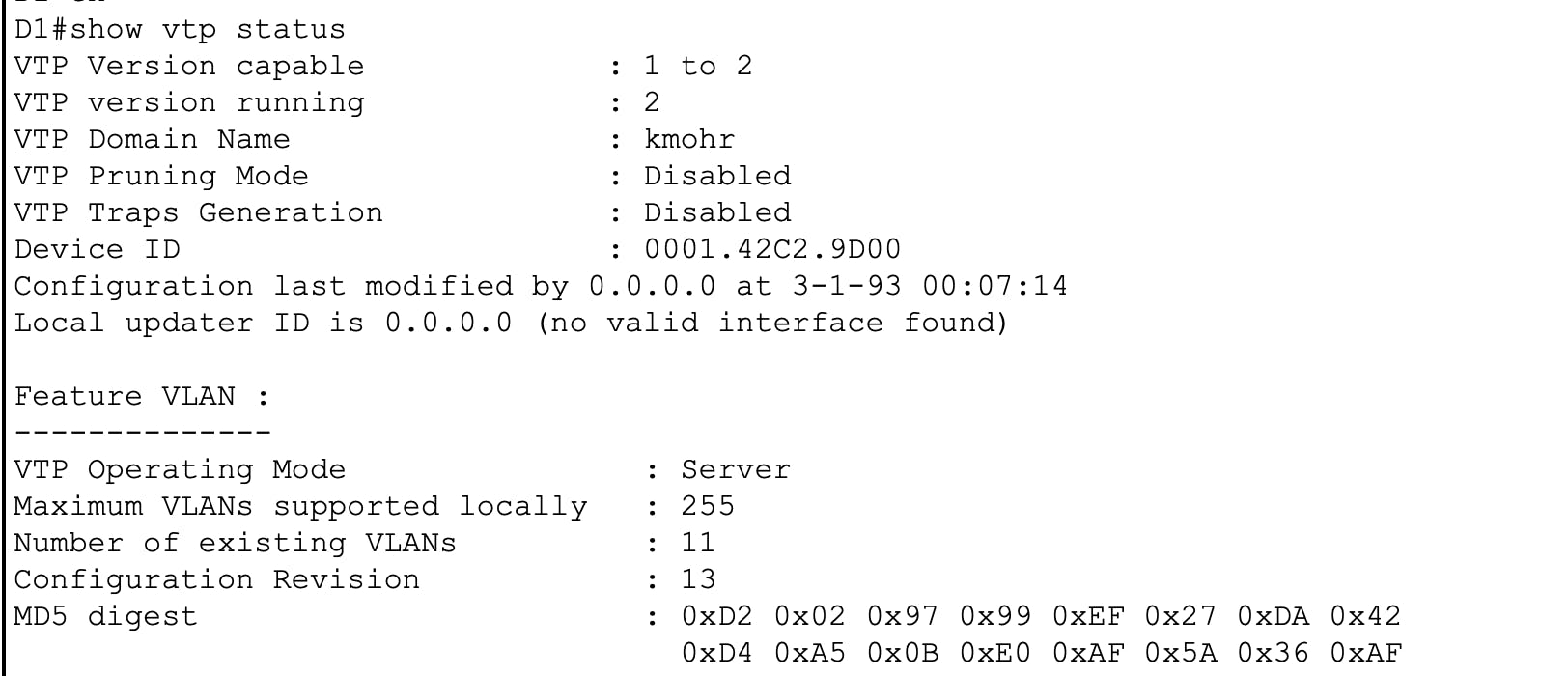
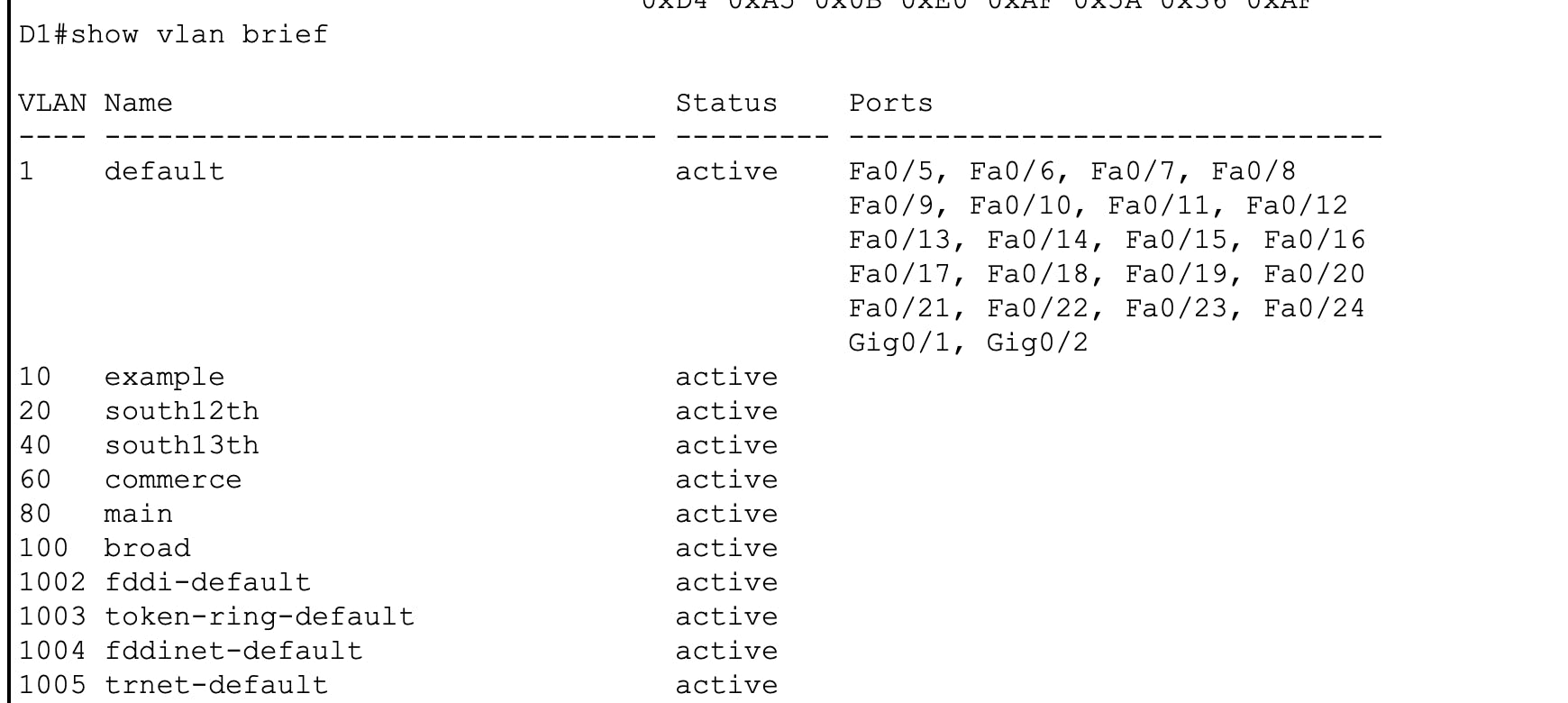
Do you now see the problem here? This is one of the big reasons why you should avoid using VTP.
Granted, Version 3 controls this problem by allowing you to define a primary server. All devices in the VTP domain will only synchronize with the primary server, no other switches, but it's still not recommended to use VTP for the very reason I just demonstrated.
You can create VLANs, but you can't do anything else...
VTP is great for VLAN creation, but that's strictly all it does. You still have to go back to each switch and assign your physical access ports to each VLAN. You also still have to manually configure trunking if you want to limit access to certain VLANs across the trunk, and at that point - VTP is just only one little thing that takes some administrative burden off your plate; you can easily write a python script to automate VLAN creation/port assignment.
More things to secure
When you introduce VTP in your network, you create more attack vectors in your network. If you use VTP versions 1 or 2, your password is saved in plaintext. When you use VTP version 3, your password is saved in an encrypted format by running the command set vtp password hidden.
VTP can also create opportunity for VLAN hopping attacks, and much worse - if someone gets hold of your VTP domain password, and you're running version 1 or 2, then someone could bring in a malicious switch and synchronize themself to your topology, allowing them to easily traverse your network. The same can be said for if the attacker were to configure their switch as a VTP server - they could send malicious VLANs out to your VTP domain if you run version 1 or 2.
Alternative to VTP
So, if you shouldn't use VTP, what can you do if you need to create lots of VLANs quickly?
Python or Ansible
You can utilize python or ansible as your automation tools. You should write an automation script to SSH to your targeted devices and run through the VLAN creations automatically.
By using a python script or ansible-playbook, you can not only create VLANs, but also run through VLAN-port assignments as well, making your life easier than having to go back and do port assignments when using VTP.
Conclusion
VTP allows you to propagate VLANs across your switched network quickly. It can remove the administrative burden of provisioning VLANs, but is it really worth using VTP in your network? No, it is not. By using VTP, you can introduce both reliability and security problems in your network. You should instead use Python or Ansible to automate VLAN provisioning.
Thanks for reading this article. I hope you found this article helpful and entertaining. Feel free to leave feedback in the comments.

